Say no to fraudulent attacks with these advanced mobile app security techniques and come up with an app that is safe and secure for the end-users.
Today, 5.19 billion people rely on mobile devices to perform a number of tasks. From paying bills to checking emails, ordering groceries to send instant messages, mobile users are simplifying their lives through smart devices. Due to the increasing demand for mobile apps, businesses of every type and size are developing mobile apps to fulfill the ever-increasing demands of the customers.
Brands use mobile apps to reach their target audience and gather valuable customer information including location, contact details, preferences, dislikes, and other useful metrics about users. This important data helps businesses to tweak important changes in their business strategy, improve their services and add more advanced functionalities to their products.
These apps contain sensitive information that encourages hackers to maliciously use this confidential information for a variety of purposes. Therefore, developers need to be extra careful when it comes to building an app for Android and iOS platforms. Unfortunately, there are many companies that don’t consider mobile app security as a business imperative and expose their company’s valuable data to risk.
Source: Hootsuite
According to the 2020 Mobile Security Index report, 43% of businesses sacrificed the security of mobile devices in 2020 and put their customers’ confidential information and business systems at risk. Many organizations are suffering a security compromise due to a lack of budget and expertise. Today, information, media, financial services, publishing and retail companies are more concerned about their customers and business data. They are ready to increase their mobile security spend for data protection and prevent malicious attacks.
Mobile app security is the key to make your digital transformation journey successful. Let’s explore how app development companies can build secure apps and prevent unauthorized users from using customers’ confidential data maliciously.
Choose only reliable third-party modules
Today the trend of using third-party libraries has become a common practice among app developers as they are under pressure to release advanced features in a very short amount of time. This is why developers rely on open-source components to build apps with unique functionality. They incorporate portions of code available to release the new feature.
Do you know using third-party libraries is not always safe? According to a Node Source study, 60% of developers don’t bother to review code thoroughly; they aren’t even confident in the security of their apps. Only 31% of developers trust the security of their own written code and feel that the code is free from vulnerabilities.
App developers are advised to intelligently choose third-party modules that are reliable and safe to use for your development project. Test the code first, as the flaws in the third-party library can give hackers an opportunity to use the code and crash the system.
Test your code
According to recent mobile app statistics, approximately 75% of mobile applications fail basic security tests. Quality assurance is the most important step of a mobile app development process to ensure a secure code. Review your code thoroughly to identify potential security issues you can’t be able to find and fix before it ends up live.
Efficient, Effective User Acquisition Made Easy
Wondering how to increase engaged, qualified new users? Get in touch with our team of user acquisition experts to discuss a custom outcome-based strategy.
Learn moreThanks to mobile app security testing tools, integrate them into your development life cycle and take maximum advantage of them to make sure your code is secure. Here is a list of some popular and reliable mobile app security testing tools, app developers can use for reviewing their code and highlighting any possible bugs.
- ImmuniWeb
- Zed Attack Proxy
- QARK
- Micro Focus
- Android Debug Bridge
- CodifiedSecurity
- Drozer
- WhiteHat Security
- Synopsys
- Veracode
- Mobile Security Framework
Hire mobile app security experts
Integrating mobile app security into your mobile app development life cycle has become the top priority for mobile app development companies. In fact, many development teams discuss their security issues with experts to get their point of view on the apps. Security experts have the skills to identify the loopholes and can significantly reduce the chances of getting compromised.
App developers should discuss their security features and learn how they will do the assessment to find possible vulnerabilities. These experts use advanced testing methods to interact with the application to check how it stores, receives, and transfers information. Your security team leverages analysis and penetration testing methods to evaluate the effectiveness of security controls. decompile the application and analyze the resulting code.
Encryption of sensitive data
Encryption is one the best ways to protect your data from any malicious activity by converting it into an indecipherable code that can’t be read by anyone else without using the secret key. If truth be told, the ultimate goal of encryption is to change the sequence of a combination lock to make the data secure. In case your data is stolen by hackers, they can’t decrypt it.
But sadly, many software development companies and enterprises don’t use encryption, which allows hackers to easily gain access to the important data and exploit it. App developers are advised to rigorously follow the method of encryption of data and check how the app’s code can be cracked.
Failure to encrypt the data can have severe consequences and lead to code theft, reputation damage, and privacy violations. So, it is recommended to encrypt all of your applications and networks for data at rest and in transit.
Manage keys carefully
Key management is the most important part of data encryption. Developers are recommended to avoid hard coding keys as they are not good for the app’s security. It is because it allows attackers to easily control the device. The safest cryptographic protocols are AES, SHA1, and MD5. Leverage cutting-edge encryption standards, such as 256-bit encryption with SHA-256 hashing for more security.
Pro Tip: Never store your keys on local devices.
HTTPS communication
Encrypting the device and the app’s code isn’t enough, development teams should also consider the channel that transmits sensitive information between the backend and device. You need to make sure the app uses HTTPS protocol with a valid certificate. HTTPS is the communication protocol that is encrypted by Transport Layer Security (TLS). Using (SSL) Secure Socket Layer is another cryptographic protocol that ensures all the data transferred across different communication channels is encrypted.
Use authorized API
There is no denying that APIs are an essential part of backend programming but for many technology companies, it is one of the major security concerns. APIs you are using for building your apps must be authorized, otherwise, it gives hackers a chance to use the information. However, using authorized APIs will help developers gain maximum security and develop secure apps.
Session management
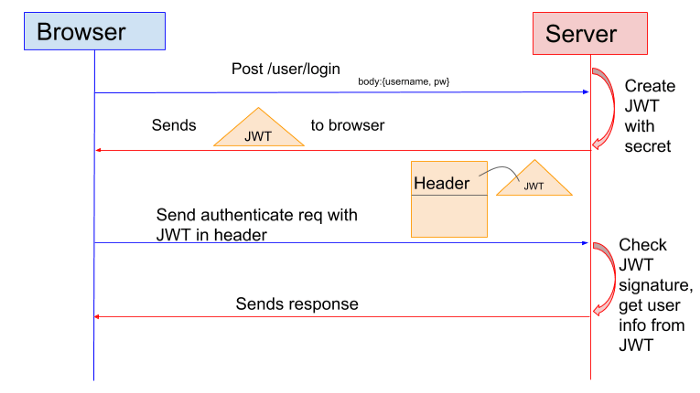
When it comes to building an app, session handling is another important aspect that needs developers’ extra attention. It is no secret that mobile sessions are longer than desktop sessions, therefore, maintaining security is essential. Using tokens is a sensible approach as they are more reliable than identifiers. They can handle user logins and effectively manage user sessions.
Token based Authentication
It is recommended to integrate the security feature of remote wipe off and log off to protect the data in case of stolen and lost devices. Furthermore, session expiration is another great option to secure the data.
Embrace tamper protection
One of the biggest problems that Android app developers face is that Android apps can be decompiled. Thanks to tamper protection which is an amazing technology that alerts you when the code is being modified. You should keep an updated record of log code changes of your mobile application. Staying on top of your log activities will help you identify whether a malicious programmer tries to inject bad code in your application or not.
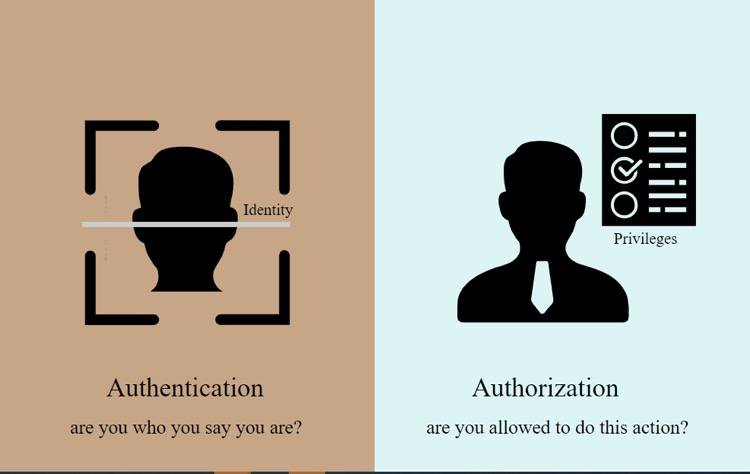
Strong authentication
Authentication is the most important factor to make your app more secure and prevent unauthorized access. Weak authentication is a security vulnerability in many mobile apps. App developers should use a multi-factor authentication approach to prevent password guessing attacks. According to statistics, only 26% of enterprises use multi-factor authentication tools to protect their applications.
You can make your app more secure by combining password-based authentication with a client certificate, OTP login, face ID, Touch ID, email/SMS code, which can lower the chances of reducing unauthorized access. Developers can also use location-based and time-of-day restrictions to prevent fraudulent attacks.
Follow the principle of least privilege
Okay, it is one of the most useful mobile app security tips for your development. Follow the Principle of Least Privilege and give access to applications and data to only those who actually need it. It is important for your app code security to limit privilege and prevent hackers from breaking the application.
Putting it into practice
Building a functional, intuitive and secure app is no easy feat. A high level of security has now become a must-have requirement in the mobile app development process. Development teams and security teams should work together to come up with a solid app security strategy to make it difficult for hackers to break the application.
Today, businesses are more aware of cybersecurity attacks and willing to invest in building a secure and hard to crack application to provide a great user experience to their customers. Applications that are secure and maintain the privacy of users’ data stand out in the app market and play a vital role in strengthening your brand image.
Attackers use multiple options to compromise your app and use your app data and credentials maliciously. Following these mobile app security techniques will definitely help you incorporate more advanced security features to build secure apps.